There’s a solution suits every devices in our LAN network, that idea is to build a fake mb3admin.com server in your lan network.
Let’s get started:
Create init script: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 mkdir /opt/mb3admin/certs -p && cd /opt/mb3admin'/CN=mb3admin.com' -addext "subjectAltName = DNS:www.mb3admin.com, DNS:mb3admin.com" -out certs/emby.crt -keyout certs/emby.keycat > nginx.conf <<EOF events { worker_connections 4096; ## Default: 1024 } http{ server { listen 80; listen [::]:80; server_name mb3admin.com; return 301 https://mb3admin.com$request_uri; } server { listen 443 ssl http2; listen [::]:443 ssl http2; server_name mb3admin.com; # Generate with command above ssl_certificate /certs/emby.crt; ssl_certificate_key /certs/emby.key; ssl_session_timeout 1d; ssl_session_cache shared:SSL:10m; # about 40000 sessions ssl_session_tickets off; # curl https://ssl-config.mozilla.org/ffdhe2048.txt > /certs/ssl-dhparams.pem ssl_dhparam /certs/ssl-dhparams.pem; # intermediate configuration ssl_protocols TLSv1.2 TLSv1.3; ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384; ssl_prefer_server_ciphers off; location /admin/service/registration/validateDevice{ default_type application/json; return 200 '{"cacheExpirationDays":3650,"message":"Device Valid (limit not checked)","resultCode":"GOOD"}'; } location /admin/service/registration/validate { default_type application/json; return 200 '{"featId":"","registered":true,"expDate":"2099-01-01","key":""}'; } location /admin/service/registration/getStatus { default_type application/json; return 200 '{"planType":"Lifetime","deviceStatus":0,"subscriptions":[]}'; } location /admin/service/appstore/register { default_type application/json; return 200 '{"featId":"","registered":true,"expDate":"2099-01-01","key":""}'; } location /emby/Plugins/SecurityInfo { default_type application/json; return 200 '{SupporterKey:"", IsMBSupporter:true}'; } add_header Access-Control-Allow-Origin * always; add_header Access-Control-Allow-Headers * always; add_header Access-Control-Allow-Method * always; add_header Access-Control-Allow-Credentials true always; } } EOF
If you run nginx server on your local network, you can just put nginx.conf under /etc/nginx/conf.d/ and restart nginx server, it will works. But if you want use docker just like me, let’s continue:
Create Dockerfile to build docker image 1 2 3 4 FROM nginxCOPY nginx.conf /etc/nginx/nginx.conf ADD certs /certs
1 2 3 4 5 6 7 8 9 10 11 12 13 ⚡ root@homesrv /opt/mb3admin
Change your DNS server 1 2 3 4 5 6 7 8 9 10 11 12 13 root@OpenWrt:~
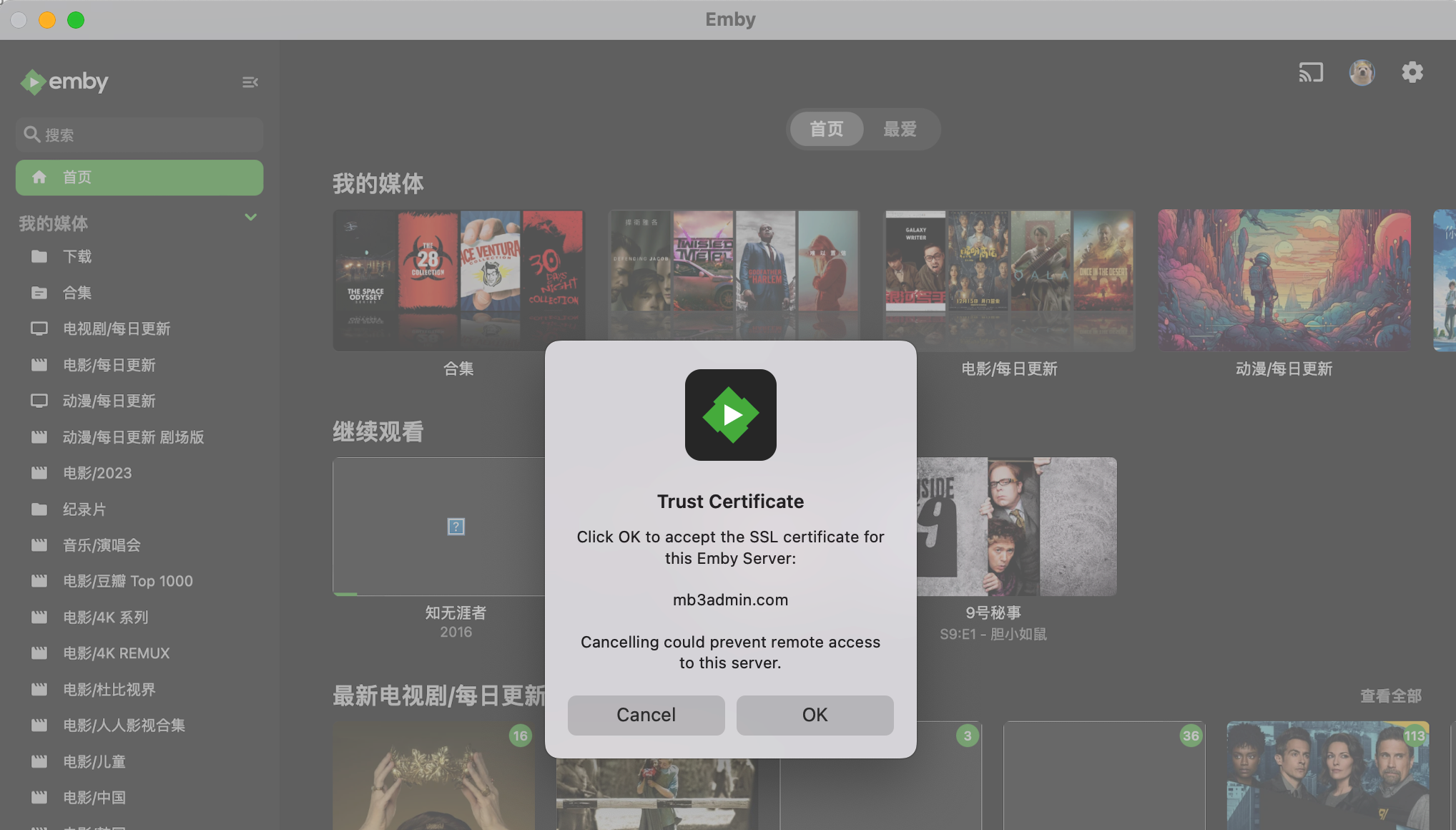
logon your emby server with emby client
When you see this page that means it worked and click OK and enjoy the moment. By the way, this is for client bypass, you should also bypass on the server side as well just like me.
Reference
https://gist.github.com/danielchc/c159626485a08c76856b2d30ae457e04